Application penetration testing software

Annie from Columbus Age: 24. A fragile and tender girl dreams of a rough embrace of a real male. Do not think about me - think about yourself, let me give you a heavenly pleasure!
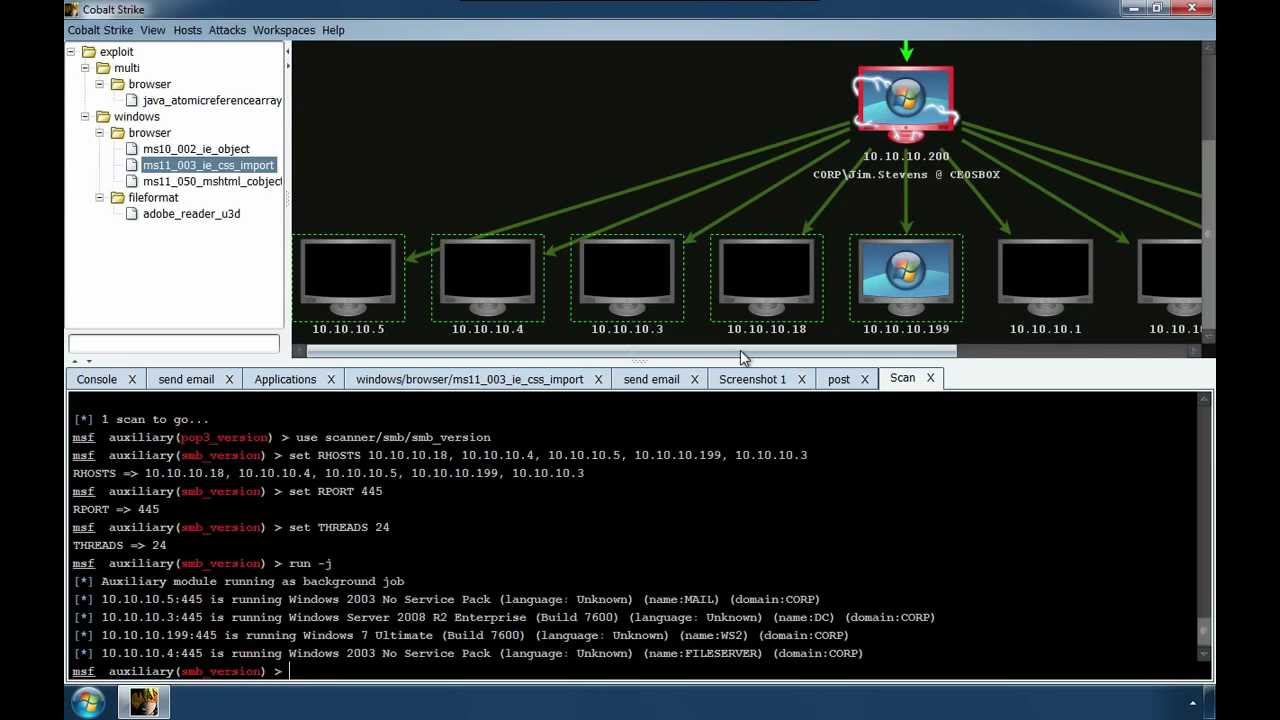
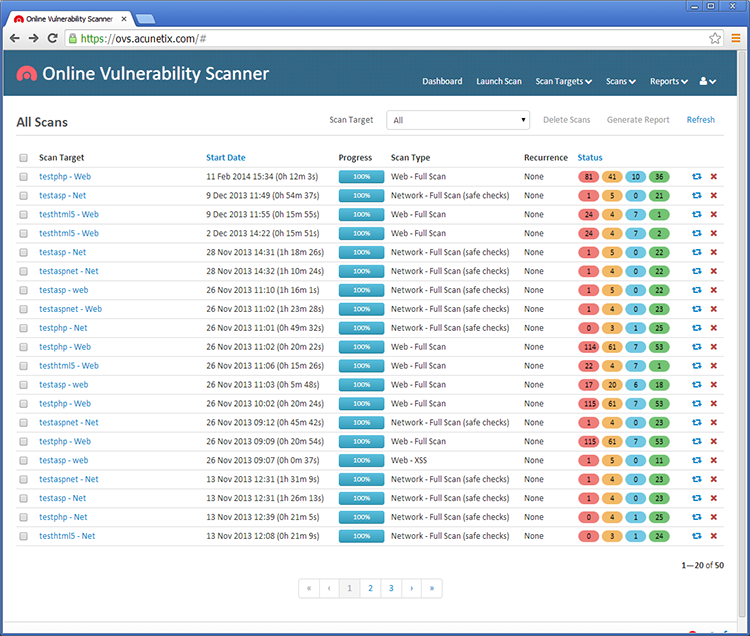
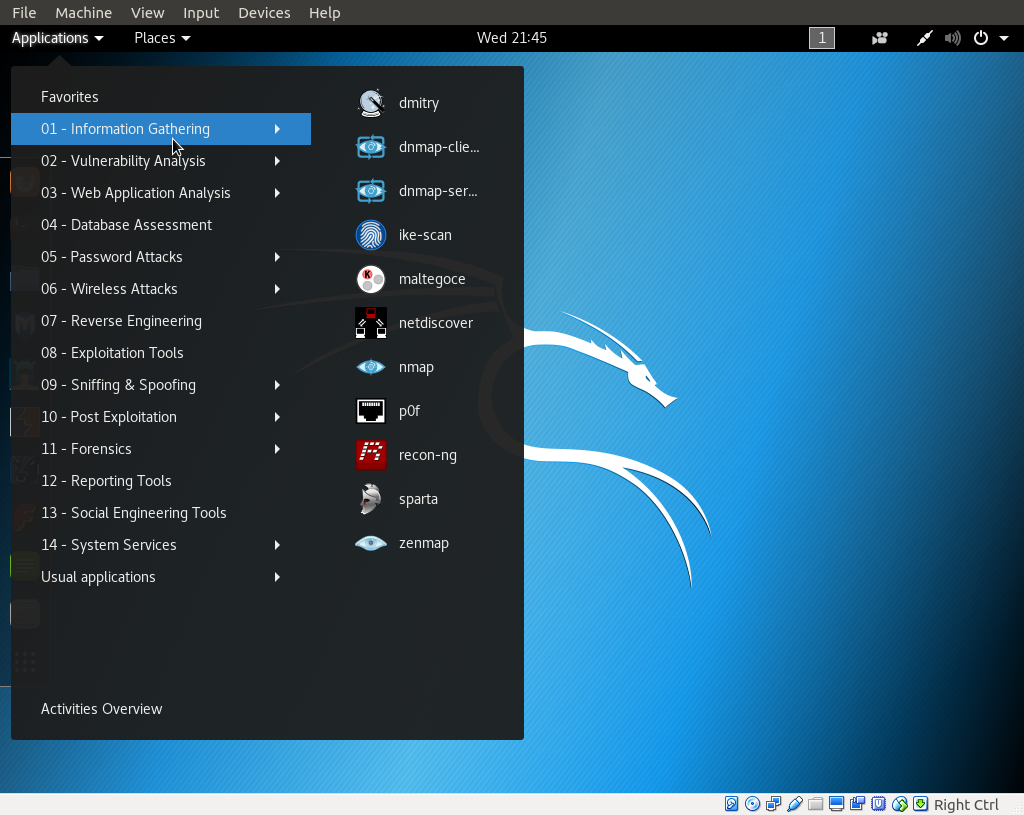
With the proper tools, a good penetration tester can automate several tasks, especially during early phases such as reconnaissance and scanning. The common steps for exploiting any target are.. It provides detailed target information that can be used by other tools such as Metasploit for exploitation. It provides comprehensive detection, including the ability to identify vulnerabilities, configuration issues and even malware on web applications. In fact, Metasploit is a framework and not a specific application, meaning it is possible to build custom tools for specific tasks. Pen-Testing Training Nikto Nikto is an open source GPL web server scanner which performs comprehensive tests for multiple items against web servers.

Penelope from Columbus Age: 28. I'm a very good girl.
Amazing Application Penetration Testing Tools
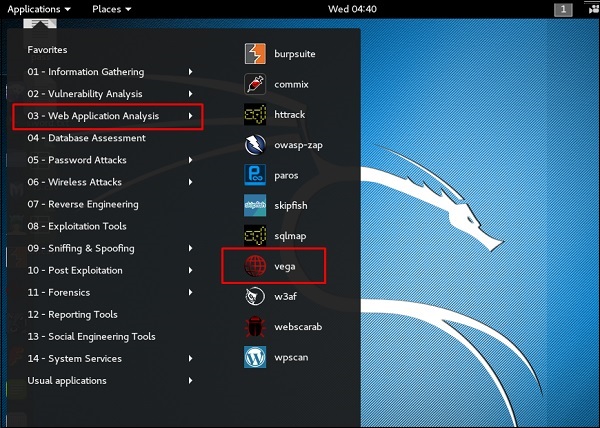
A word of advice for pentesters. Nikto was not designed with a stealthy approach in mind. I'm not interested in training To get certified - company mandated To get certified - my own reasons To improve my skillset - get a promotion To improve my skillset- for a new job Other. This data can then be used by other tools such as Metasploit for exploiting web applications. With a comprehensive list of plugins and very efficient features, it is capable of deeply scanning applications to collect data and responses from the server.

Rachel from Columbus Age: 30. Hi!) I would like to meet an interesting, passionate man.

Nikki from Columbus Age: 28. In search of an adequate, attractive man, lover and friend in one person who likes variety in sex, I'm sexy, slim, uninhibited, I love sex.
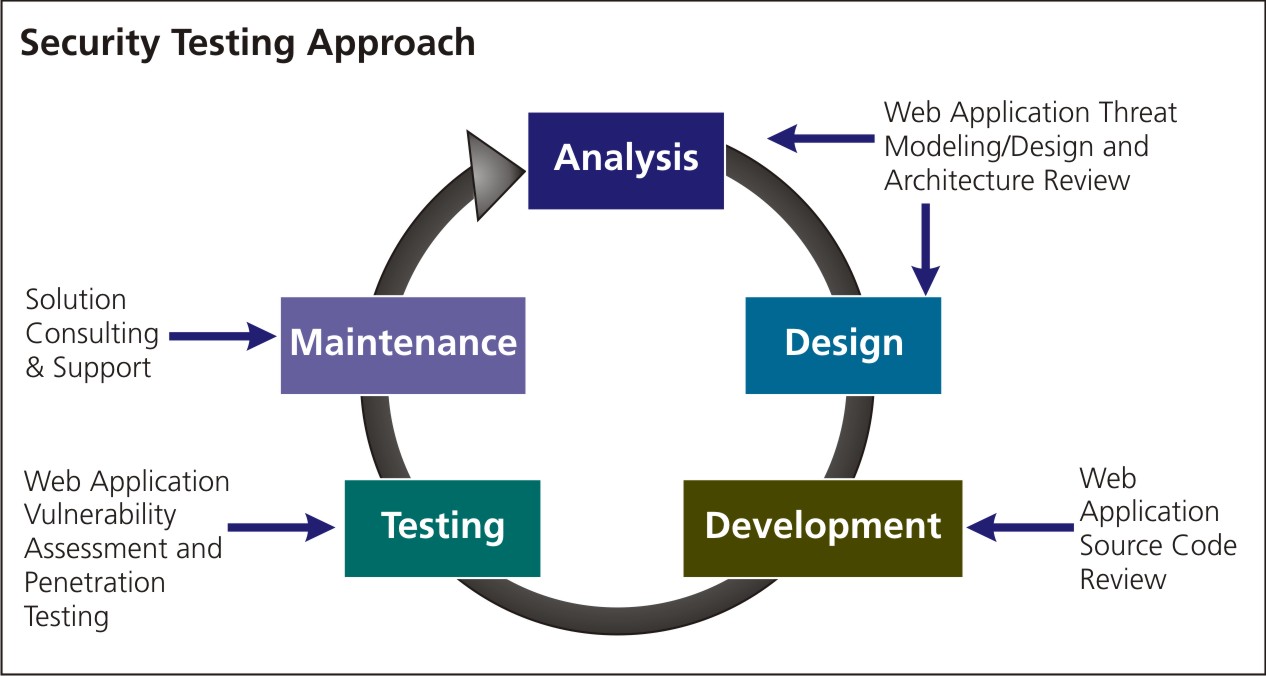
The state of application penetration testing
For manipulating and resending individual requests Sequencer tool. Nmap also includes a scripting module, so it is not limited to gathering basic information. The common steps for exploiting any target are. Burp Suite Burp Suite is an integrated platform used for testing the security of web applications. This is when your focus is on mapping your targets and discovering any exploitable vulnerabilities.

Lori from Columbus Age: 34. I am different... I'll be whatever you want me to be.